Hello, everyone. Today we're going to design a complex cloud architecture for a multi-national law firm that is in dire need of a solution to their network and expansion problems. It was disclosed that the company has offices across the world and is looking for a more concise and cost-efficient way to go about its rapid expansion.
- The firm has data centers located in New York, USA, and London, UK.
- data centers leverage a redundant ethernet connection between them which they load share.
- Each link is at 30 % utilization and rising.
- The firm has around a petabyte of data in object storage ( scan documents, pdf, case files, pieces of evidence, etc...)
- Critical security requirements were brought up, as well as at least four 9's of availability.
Now that we know a little bit more about the situation, there're many ways we could go about this. In cloud computing, there are usually three ways or configurations you could go about handling your data centers. That is everything on-premise, hybrid (one foot on-premises and the other in the cloud, either single or multi-cloud), or going completely in the cloud
The firm is operating completely on-premises and is considering moving to the cloud in other to leverage its scalability and agility. Going multi-cloud here wouldn't be a bad idea but it would be overkill because not only it would add more complexity to the routing, it would also make storage a little more difficult, despite the bargaining power and flexibility that comes with going multi-cloud. For that reason, I decided to go with a hybrid configuration and muli-cloud (only to a certain extent).
Now, the company also mentioned a need to keep the New York and London data operations separate and only share data when needed while keeping an acceptable level of integrity between the two sites. Because of that, going hybrid with one site on-premise and the other in the cloud, and another cloud for disaster recovery seems like the solution here.
To go about this, we will first consolidate the UK and US data centers into one, and turn it into an OpenStack or Nutanix cloud to then finally connect it to a bigger cloud. This way, we'll have the UK move completely to the cloud and use it for disaster recovery in the US. We will use AWS cloud as my cloud provider for this architecture, and Azure as a backup. This will provide a more concise and cost-efficient solution as it'll leverage all the current servers and storage they already have. Also, as a multi-national law firm, they need the best performance connection between the data center in New York and London. Meaning for both clouds, we'll need a direct connection that will leverage iBGP protocol, and an encrypted VPN connection as backup, with a VPN concentrator and a redundant internet connection in case the internet provider has an outage.
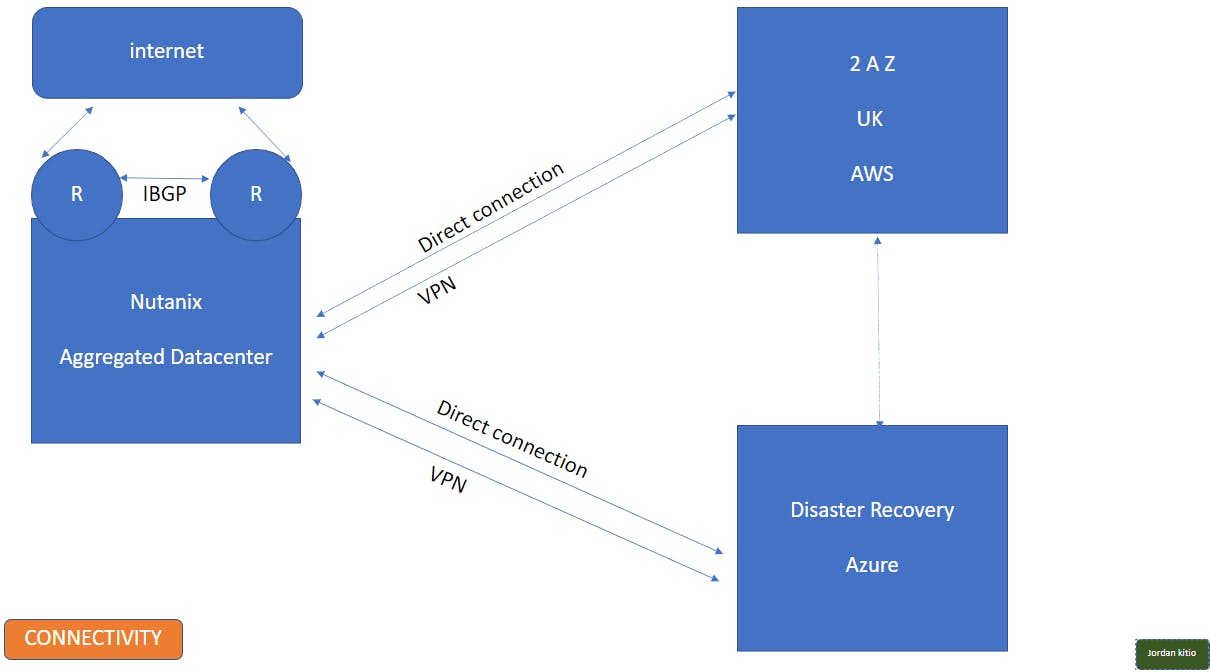
The type of data in a business usually dictates the requirements for disaster recovery. Because we're dealing with a law firm here, 45 minutes to an hour of downtime will not be a major killer. If anything goes wrong with AWS Cloud, Microsoft Azure will become the central cloud, in a passive-active strategy. Meaning, we keep small instances up and running in Azure in an Autoscaling group.
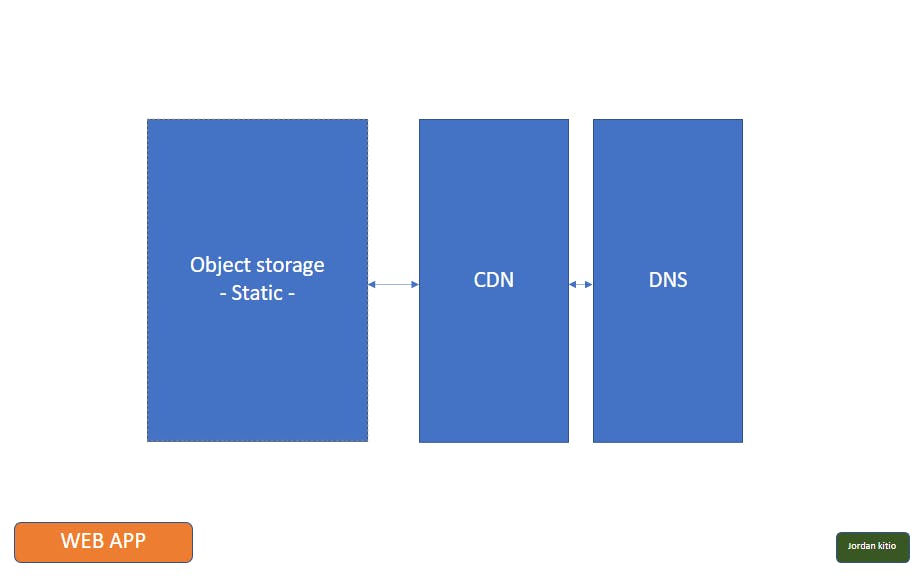
As for their website, we know it's going to be mostly static, so it will be hosted on object storage, along with a CDN and redundant DNS service In the cloud. The reason is that since we're working in a hybrid and somewhat multi-cloud environment, we need requests to be routed appropriately. In addition to that, they will be working with legal applications in a shared environment, and for that, they'll need a virtual machine to house them. They'll also need somewhere to host their applications, so they'll need virtual machines. Since they working in a shared environment, they'll also need an NFS. Both the NFS and the applications will be running on virtual machines and because of that, we'll also introduce an application load balancer.
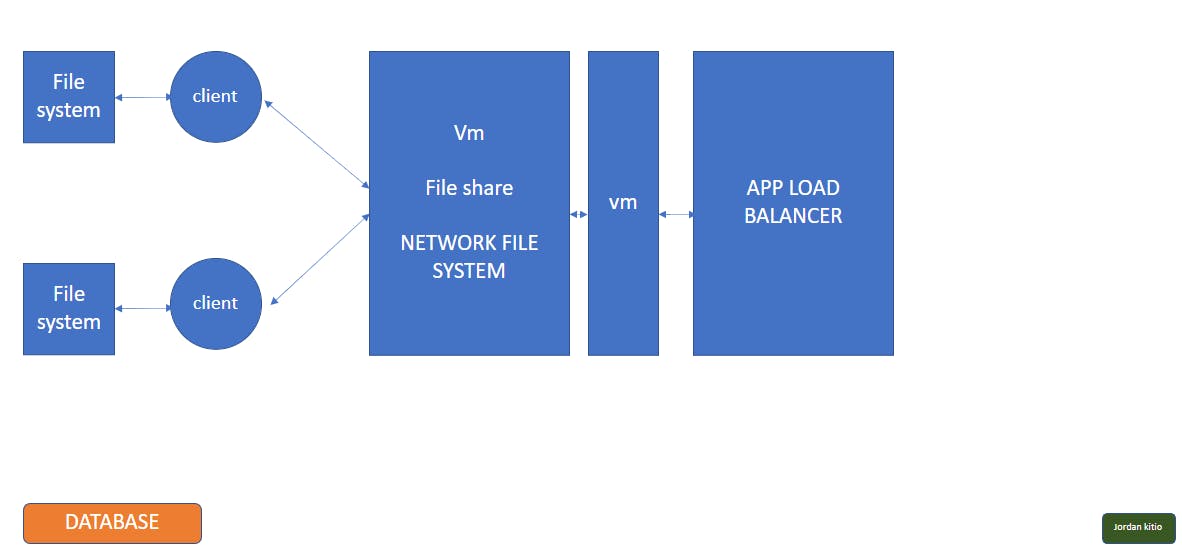
Now let's talk security. One of the requirements the firm communicated to us was the necessity of a critical and robust security system. They are dealing with critical documents and data that don't need to be accessed by just anyone. First, we're going to mount a CDN as mentioned earlier. This way we will keep the system from seeing invalid requests, and block them out before they reach it. We don't want any traffic from the internet to reach our network, so well also have a firewall. On top of that, we'll also mount an IDS/IPS along the firewall to get us additional information and security across our network. It's important to note here that these services will be running on their own virtual machine thus we'll need a Network load balancer to load share traffic across these various services. Along with the firewalls we also want to keep unwanted traffic out of our subnets here, so we'll need an Access Control List. For our webservers, will need to Security group to keep unwanted traffic from reaching them. With all these security measures in place, we're able to provide our firm with a robust system that'll prevent unwanted traffic to reach them. Finally, AWS AD will manage users both in the cloud and on-premises, adding an extra layer of security to user names and passwords using Multi-Factor Authentication (MFA) and all our public services will be running In a DMZ (demilitarized zone) in other to keep the internal and private networks separated from the external network.
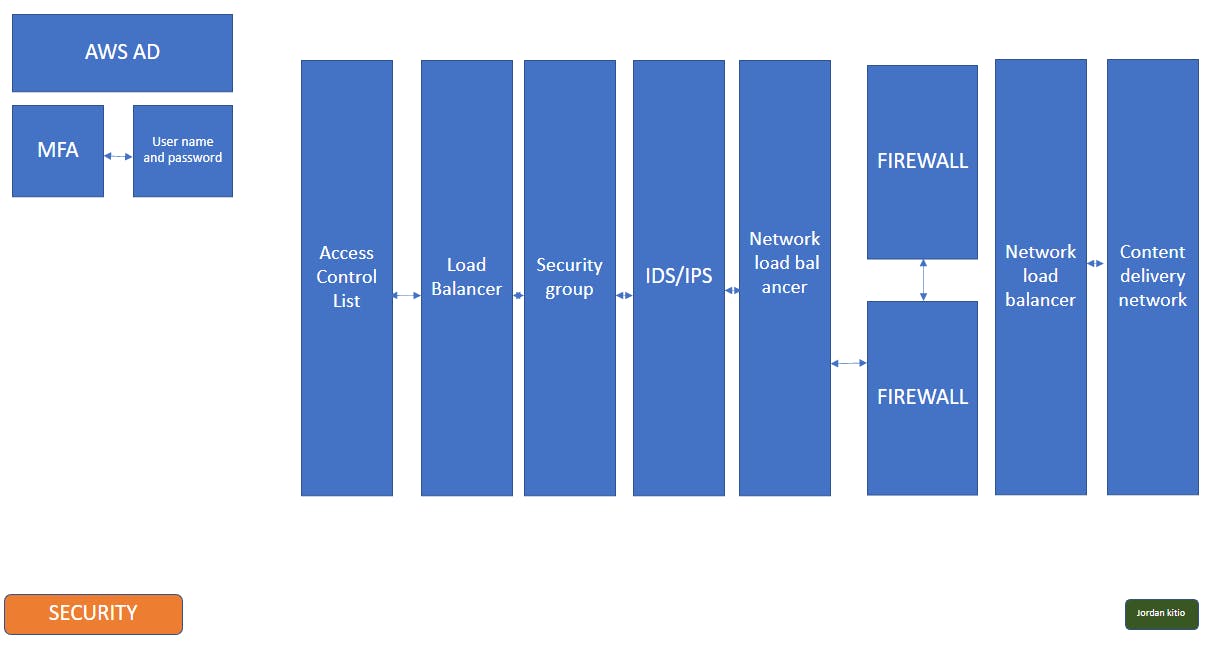
Adopting this architecture has allowed the law firm to tap into a much smoother growth while keeping their data secured at all time.
This is a high-level illustration of the design; the full layout would be far more elaborate and sophisticated, as a broader public is the intended audience.
Thank you for reading, and see you next time for more cloud architecture !!!
Jordan